What does Cybersecurity for Manufacturers Involve?
Cybersecurity concerns the protection of sensitive information stored and passed through computers, networks, and programs. There is a range of preventative techniques that involve physical security of information as well as cyber. This protection is against unauthorized access, disclosure, use, modification, or destruction. Cybercrime can take many different forms, but each has the intent of accessing information to exploit financially, politically, or to cause disruption and fear.
Kaspersky Labs reported in early October 2017 that manufacturers were the most susceptible to cyber threats, accounting for one-third of all attacks. Online Trust Alliance reports that cyber attacks have nearly doubled in volume since 2016. According to the U.S. Department of Homeland Security, manufacturing is the second most targeted industry.
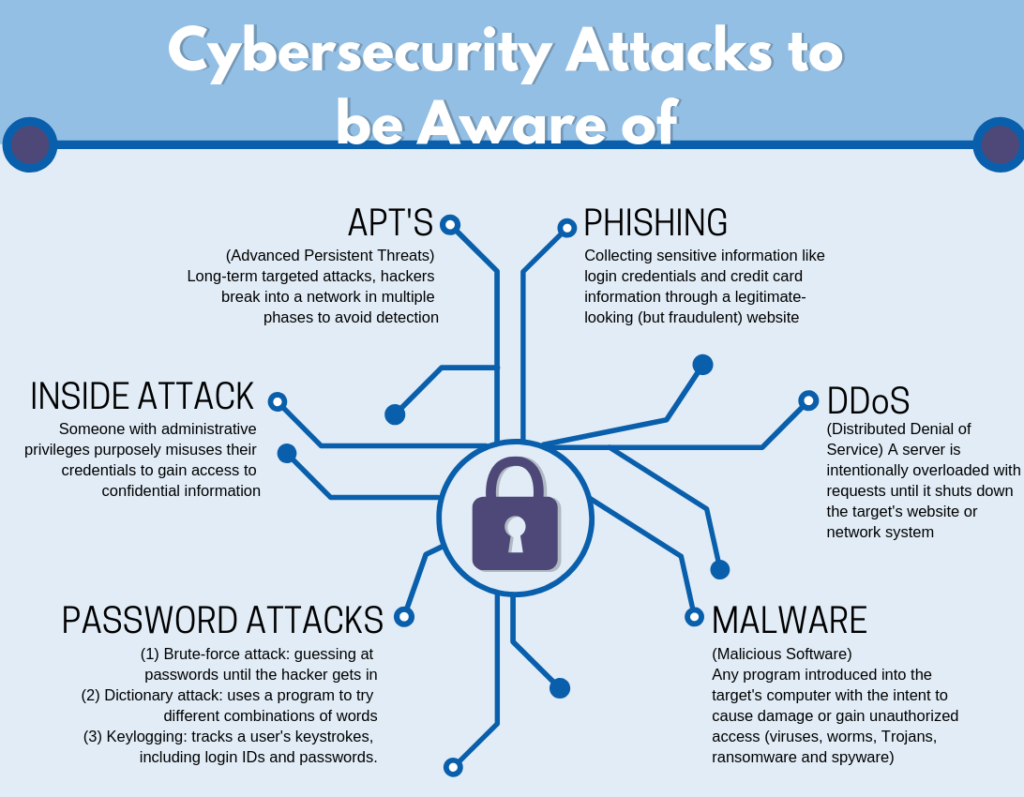
A New Target: Small to Medium Sized Manufacturers
While larger manufacturers, financial institutions, and tech companies have generally been the target of cyber-attacks, they have responded to these intrusions with increased protections and cybersecurity plans and protocols. Large companies may have more to lose in terms of volume, but most small businesses go out of business within six months of a cyber-attack. Why would criminals work harder to gain access to securely protected facilities when they could easily target those who think they have nothing of value; small to medium-sized manufacturers. Not only do many SME’s have data they don’t think anyone would exploit, but they are also entry points to larger supply chains.
The classic example of this was back in 2013 when hackers got access to Target’s Point of Sale machines through an HVAC supplier who was accessing Target’s network with an external vendor portal. Hackers gained access to over 40 million customer credit card credentials and 70 million customer records were affected across the United States. Believe it or not, by today’s standards, Target’s breach was small, but it was one of the first that took many by surprise.
When cyber-attacks happen, companies become liable for exposing customers’ intellectual property, employee and customers’ personal information, or even transmitting a virus to another facility. This does not include the costs that are then incurred by the company for loss of productivity, contracts, and physical and reputational damage.
Why SME’s are Falling Behind
There has been a lag in addressing these issues by manufacturers because there are no blanket procedures everyone can adapt to become secure. Each company requires an analysis of the threats and vulnerabilities specific to their operations and each solution is different. Just like ISO 9000, companies have been slow to adopt new standards, but similar to quality, cybersecurity needs to be a living breathing part of the company.
Small to medium-sized manufacturers tend to be particularly vulnerable for the following reasons:
- Less likely to have strict protocols
- Use of outdated equipment and systems makes them more vulnerable
- Don’t have cybersecurity-related policies in place
- Are not educating employees what to watch out for
- Lack of skilled employees (an on-going problem in the current manufacturing space) increases the chances they will fall for a targeted attack
- Not isolating their industrial control system networks from their standard network
- Store intellectual property and other data that can be ransomed, stolen, or extorted
- Have become the low hanging fruit for cybercriminals since their initial targets have increased security
As of December 31, 2017, all Department of Defense contractors were required to comply with the DFARS Cybersecurity Requirement. This means they needed to provide security to safeguard defense information by implementing the security requirements in NIST SP 800-171 rev 1. It requires contractors to develop a security plan, conduct an assessment, produce an assessment report, and then create a plan of action.
NIST??
The National Institute of Standards and Technology (NIST) is a non-regulatory agency of the U.S. Department of Commerce that serves as the U.S. National Measurement Institute. NIST does not regulate cybersecurity but has provided guidance in the form of reference materials that government agencies and industry organizations typically utilize. While NIST’s cybersecurity standard has become a requirement for defense contractors, the same standard is being adopted in the automotive supply chain as well. In fact, NIST’s Cybersecurity Framework (we cover more about this below) is expected to be used by 50% of organizations in the United States by next year alone including industries such as healthcare, financial services, and retail. These kinds of standards are becoming more prominent as industries realize their vulnerabilities.
For manufacturers who do not have contracts with the Department of Defense, there are still many reasons, as stated above, to invest in a cybersecurity plan. Just because a company is not working specifically with files the government says need safeguarding, does not mean that they do not store information that could be stolen and exploited. The reality is, most companies have already been hacked whether they realize it or not.
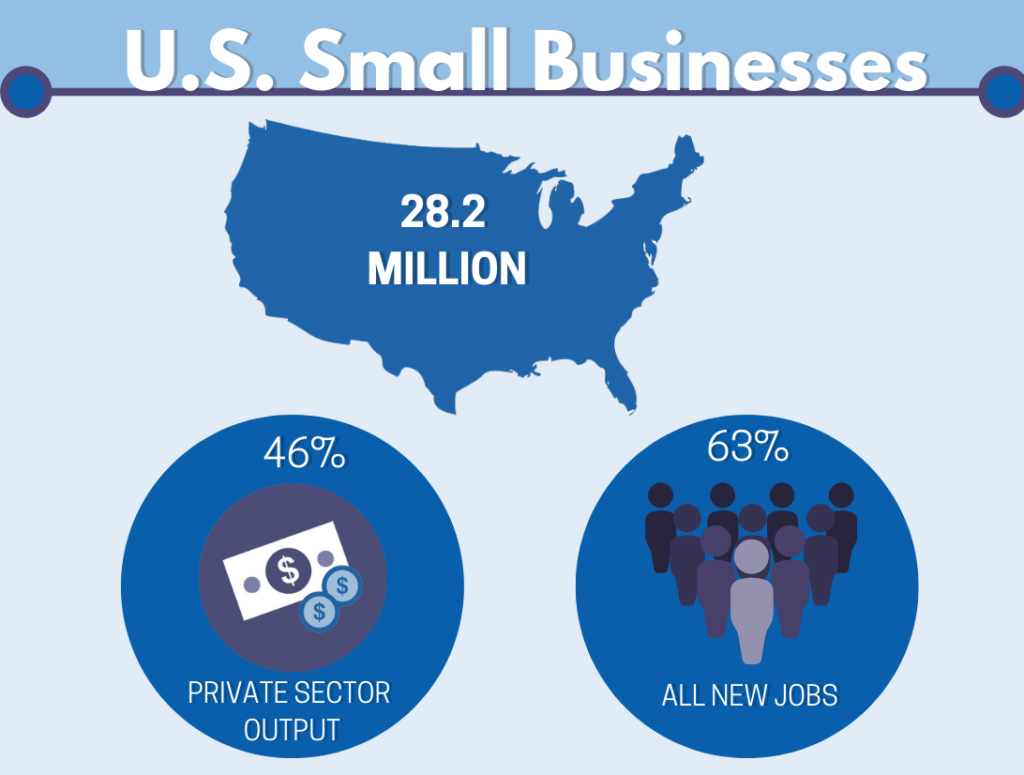
According to the Small Business Administration, there are 28.2 million small businesses in the United States. These businesses produce approximately 46 % of our nation’s private-sector output and create 63% of all new jobs in the country. Due to the threat a cyber breach puts on the success of small businesses, it is that much more important that they understand and manage these risks.
NIST’s Cybersecurity Guide for Small Businesses
In addition to NIST’s 800-171 standard, they have developed the Fundamentals for Small Business Information Security. This document outlines how to create an information security program with language that is less technical. Meaning, business owners who do not have a background in computers will have the ability to effectively use and understand it. This resource is different from the security requirements laid out for DOD contractors in NIST SP 800-171 by being more of a guide for better business practices than a pass or fail assessment.
What NIST titles the “Cybersecurity Framework” are steps to work through the process of safeguarding information. These are actions that should be used on a continual basis throughout the organization. There are five core functions of the cybersecurity framework:
- Identify: Develop an understanding of who in the organization has access to what information and put the proper controls in place. It involves identifying what accounts have access to what kinds of information, conducting background checks, creating individual user accounts, and putting in place policies and procedures for information security expectations (such as in an employee handbook).
- Protect: Develop and implement safeguards necessary to prevent or contain the impacts of a cybersecurity event. It involves limiting employee access to data, installing surge protectors and uninterruptible power supplies, patching/updating applications regularly, activating software and hardware firewalls on all business networks, securing wireless access point and networks, setting up web and email filters, encrypting sensitive data, disposing of old computers and media properly, and training new hires.
- Detect: Develop and implement activities such as malware programs and logs to detect a cybersecurity event
- Respond: Develop a plan with a goal to contain or reduce the impact of a cybersecurity event as well as types of activities that determine an information security incident has taken place. Plans should include who has what roles and responsibilities, what to do with your information system, and who should be notified when.
- Recover: Develop and implement activities that help to restore what may be lost from a security event. Backups of important business information should be made and tested regularly.
Training Employees – Everyone has a Responsibility
As identified previously, cybersecurity needs to become a part of the company culture. It is not an area that only the IT departments should be concerned with. A 2018 study showed that more than 40% of senior executives and small business owners reported employee negligence and accidents as the root cause of their most recent data breach.
More often than not, this is because employees are simply not made aware of what they should be looking out for or do not understand how they are creating vulnerabilities in their company. Things, like clicking on questionable links, downloading unauthorized software, and sending sensitive information to spoofed email addresses, are all actions that are easily avoidable when employees are trained properly. Because of this, there are simple ways to begin implementing cybersecurity protocols today.
Within NIST’s Fundamentals for Small Business Information Security document, there are a number of day to day action items that companies can begin with to protect themselves from cyber threats in more basic ways, some of which are:
- Be careful of email attachments and web links – do not click on a link or open an attachment that you were not expecting, malware is most commonly distributed this way, sent pretending to be someone you know. Call the sender to verify before opening. Hover over links before clicking to see if you recognize the address.
- Use separate personal and business computers, mobile devices, and accounts – as much as possible especially if other people use your personal devices. Keep personal activities to personal devices and business activities to business devices.
- Do not connect personal or untrusted storage devices or hardware to your computer, mobile device, or network – do not share USB or external hard drive between personal and business devices and disable AutoRun features for USB ports and CD and DVD drives
- Be careful downloading software – do not download from unknown websites
- Do not give out personal or business information – social engineering is a common way cybercriminals attempt to gain access to business information by pretending to be someone they are not.
- Watch for harmful pop-ups – do not respond to popup windows, use a popup blocker, and only allow popups on websites you trust
- Use strong passwords – random sequence of letters, upper and lowercase, numbers, and special characters at least 12 characters long. Use multifactor identification for applications with important information.
- Conduct online business more securely – use secure browser connection (indicated by small lock in lower right or upper left of browser) when doing online business/commerce/banking
Cybersecurity threats affect businesses of all industries, but the data shows that manufacturers are increasingly being targeted, and those who don’t think they have much to lose are often the easiest targets, with practically have everything to lose. The cost to assess a company and implement changes to protect against cyber threats is far cheaper than the potential loss from a cyber breach. Be proactive, don’t wait until it’s too late.
If you have any questions regarding cybersecurity and your business, we are always here to help! Contact our IT specialist today:
(845) 391 – 8214 x 3003
Jacob.ernst@hvtdc.org
