MTEC is a New York State MEP Center with the capability of providing cybersecurity assessments, remediations, and IT consulting services at a subsidized price compared to independent service providers. If you are interested in hearing more about what a cybersecurity audit can do for you, email Alexis Wilson at alexis.wilson@hvtdc.org.
The Cybersecurity Maturity Model Certification, or CMMC, is the emerging standard for cybersecurity being deployed by the Department of Defense. The 5-level model is broken down on a matrix of categorized practices and processes on a scale of least stringent to most stringent. The purpose of this model is to create a hierarchy of manufacturers and, based on how optimized their practices are, permit them to bid on higher-level contracts.
Truth be told, this is all we can really be sure of when it comes to CMMC.
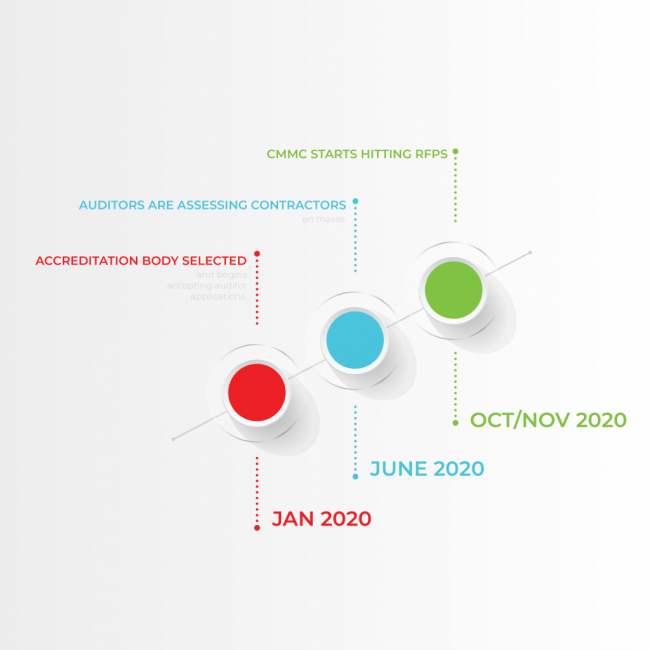
As of early January 2020, the document that is intended to eventually become the final form of the model is currently in v0.7. While the final version is predicted to be released by the end of the month, there presently is no finalized form available to base any substantial training or auditing on. It is estimated that third-party auditor training is set to begin in the middle quarters of 2020 with auditing certifications set to be available at the end of 2020. Any company that is claiming to be capable of providing CMMC auditing as a service currently is a little ahead of their skis so be wary when looking for assistance assessing.
However, one thing we do know that provides a little guidance moving forward is that the NIST SP 800-171 Guideline is still playing an integral role in the framework of CMMC.
It is still heavily recommended, at least until the final version of the CMMC document is released, to continue to maintain your systems at the NIST SP 800-171 Guideline. This means that at the very least, every company should at least have some sort of assessment performed either in-house or third-party that demonstrates recognition of system vulnerabilities. It is also required in the guideline to implement a System Security Plan and an Action Plan in order to be considered “compliant”.
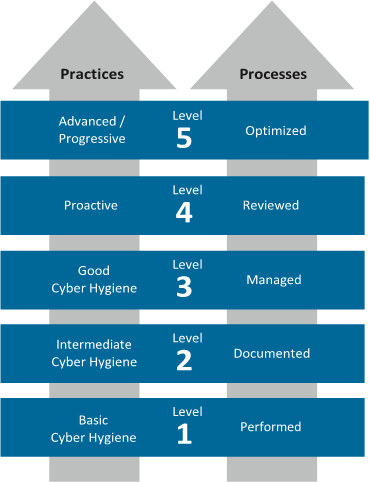
At this point, being up to the NIST SP 800-171 Guideline will put a company in a good position to transition to a Level 3 on the five-level spectrum. As the diagram exhibits, Level 3 suggests that company processes are being managed and they are displaying ‘Good Cyber Hygiene’.
The beauty of the new matrix is that it allows a company to determine what compromise between convenience and security best fits their business practices. The spectrum also allows for small businesses to identify a place for themselves. Having this foothold, even if it is performing the most basic of practices, creates a foundation for further growth of business security.
The DoD has stated that its intention is to deliver Version 1.0 of the CMMC Framework by the end of January 2020. Similarly to the DFARS Cybersecurity Clause, the requirements from the CMMC Framework are expected to start trickling down the supply chain as early as Fall 2020.
At MTEC, we say the best place to start is an assessment against the NIST SP 800-171. Either in-house or through a third-party provider, an assessment shows your vulnerabilities and deficits which help layout a Plan of Action that can be tailored to each business depending on what resources are ready to be allocated to the project.
Achieving any sort of cyber compliance is no small undertaking. in our experience performing assessments, businesses that are successful in achieving compliance often have a committee or team of individuals working on the project that is closely backed by management. In addition, there are some steps that you can take right now to start preparing for an assessment. First, start documenting your current practices and procedures. When you go through an assessment, a thorough auditor will ask to look through these documents to see if they meet the current standards set forth by the guideline. Next, it is simple (and free) to toggle group policy settings on your domain controller. Your IT personnel should be able to look through the standard and determine which settings can be deployed immediately. Lastly, physical security is an important section that is commonly failed. Physical security adjustments can sometimes be costly, so for budgeting purposes, it is good to start considering that entrances to the building and server room need to be locked and access needs to be able to be tied to a specific user.
If you have any questions regarding cybersecurity, NIST SP 800-171, CMMC, or to schedule an assessment, email Alexis Wilson at alexis.wilson@hvtdc.org.