Does my business qualify for R&D Tax Credits?
As a manufacturing company, at some point or another, you’ve dedicated resources to research and development whether you realize it or not. There are several activities that could qualify as research and development including: Attempting to advance technology in a well-defined way Finding a new approach when, despite your expertise, the approach was not obvious […]
Preparing for CMMC: A Contractors Guide to Setting up for Cyber Success
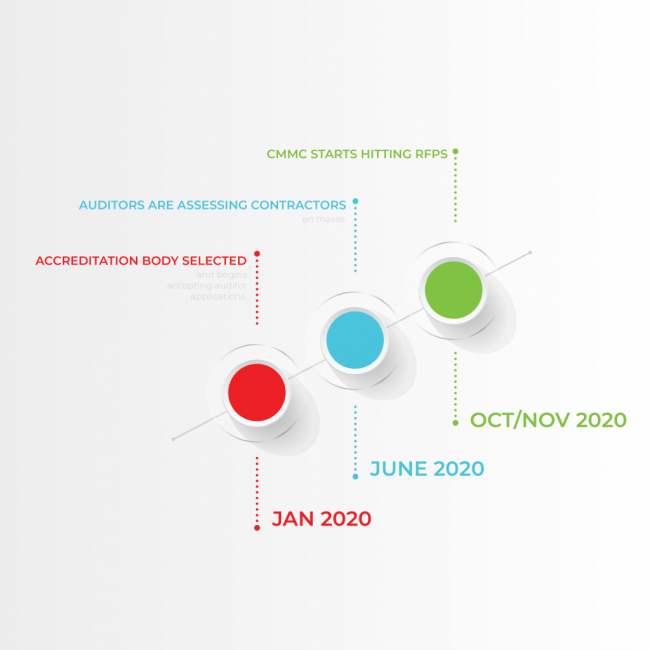
MTEC is a New York State MEP Center with the capability of providing cybersecurity assessments, remediations, and IT consulting services at a subsidized price compared to independent service providers. If you are interested in hearing more about what a cybersecurity audit can do for you, email Alexis Wilson at alexis.wilson@hvtdc.org. The Cybersecurity Maturity Model Certification, […]
Press Release: MTEC completes a round of cybersecurity assessments with DoD manufacturers

FOR IMMEDIATE RELEASE Contact: Alexis Wilson, MTECPhone: (845)391-8214Email: alexis.wilson@hvtdc.org Alert: Your Data Has Been Compromised (Highland, NY) — Cybercrime is making headlines in a big way. What first became a concern in 2005 is now making daily news. From Target to Equifax to Dunkin Donuts, the companies that you trust every day to secure your […]
What To Do After a Data Breach

You thought you had done everything you needed to protect your business but your company ultimately fell victim to a data breach. You’re not the first and DEFINITELY not the last. However, it isn’t always necessarily the data breach that sends a company underwater, it typically falls in the hands of how a company handles […]
Cyber Summer: Penetration Testing

Penetration testing is growing in popularity due to the increased interest in data privacy. Small businesses are the perfect target for these attacks because they’re more likely to have a door open on their network that could give an attacker entry into customer data. Read more to learn about penetration testing and how it can […]
Cyber Summer: Rogue Access Points

Q: What are rogue access points? A: Rogue access points are wireless access points disguising as a genuine access point. Attackers will deploy these near the real access point in hopes they trick someone into connecting to them. Often the access point will seem legitimate and allow full internet functionality, but in the background, an […]
Tiles for Hope is in the business of rebuilding homes and transforming lives

Lisa A. Edwards and her dog, Skipper Doodle, serve as the face of a small company with a big mission. Tiles for Hope functions under the umbrella of Lifestyle to Independence, of which Lisa is the sole proprietor. As with many passionate people, Lisa’s story is filled with trials and tribulations which make her mission […]
Cyber Summer: IoT + BYOD

More simply put, the Internet of Things (IoT) and Bring Your Own Device (BYOD) are two concepts that have been on the rise and show no signs of stopping. With the boom of AI technology, smart devices are becoming more and more a crucial part in the daily routine of the average person. However, what […]
Cyber Summer: Safe Passwords and Security
In the last edition of Cyber Summer, we reviewed social engineering and the many ways a hacker can manipulate information out of an individual. This weeks topic is safe passwords and security. Passwords are your first line of defense. If a hacker can’t access your information due to a strong password, that’s more than half […]
Cyber Summer: Social Engineering

In the last edition of Cyber Summer, we reviewed safe internet browsing and what you can do to preserve your privacy while searching the web. This weeks topic is social engineering. We’re sure something below will sound familiar… Q: What is social engineering? A: Social engineering is a very broad topic. In essence, it is an […]